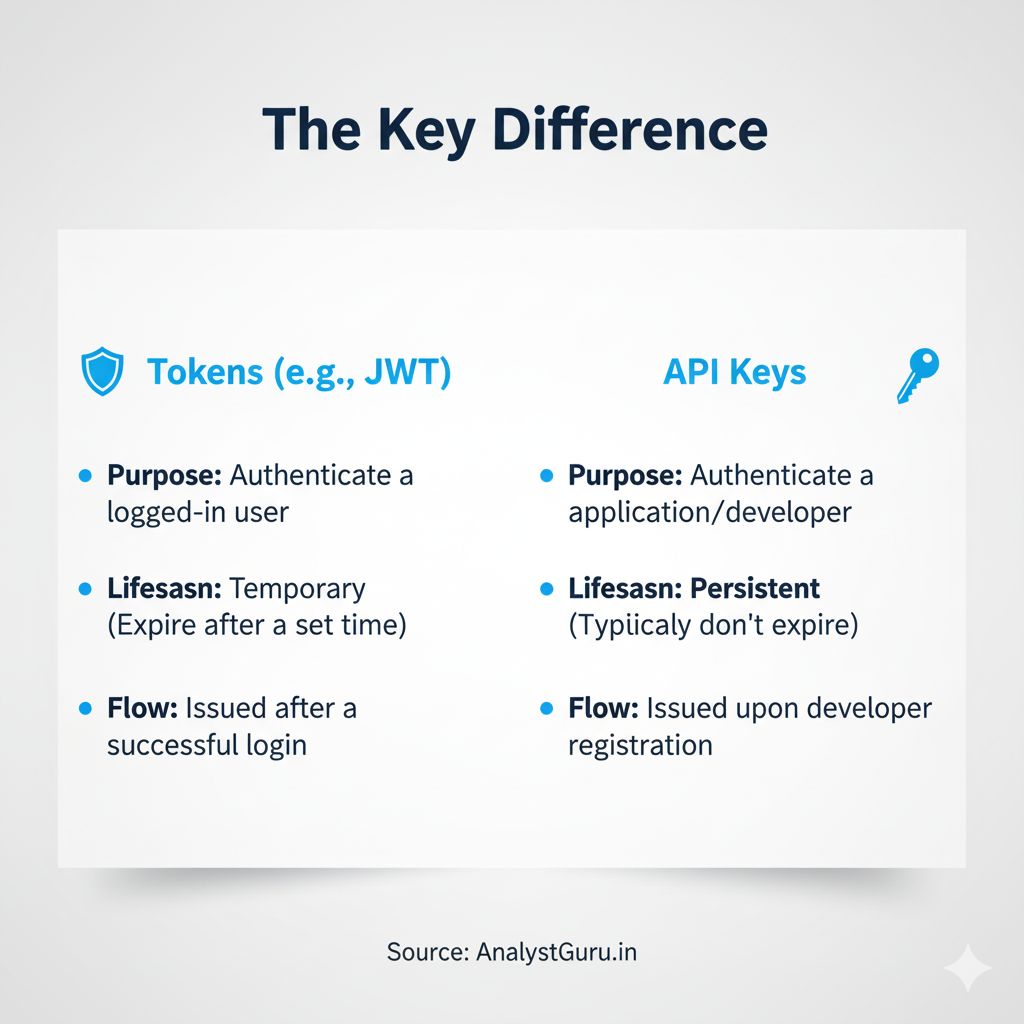
In the world of data and services, authentication and authorization are the gatekeepers ensuring only the right people (or programs) get access. If your website, AnalystGuru.in, deals with data and analysis, you’ll constantly encounter two key tools used for this purpose: Tokens (like JWTs) and API Keys.
While both are used to verify identity, they serve different masters and follow distinct processes. Let’s break down the simplified flow for each and clarify their roles.

🔑 The API Key Flow: Access for Third-Party Developers
Think of an API Key as a permanent, unique “ID card” or client secret given to an application or developer. This is typically used when a third-party application wants to access your public services.
Simplified API Key Flow:
* Registration: A 3rd party developer registers their application on your Developer Portal.
* Key Issuance: The portal generates and issues a unique API Key to the developer. Crucially, this key is also stored in a secure key store for later verification.
* Request: The developer’s application sends API requests, including the API Key in the header.
* Verification: Your API Gateway intercepts the request and sends the key to an API Key Validation service.
* Validation: The validation service checks the key against the secure key store and responds to the gateway.
* Access: For valid API keys, the gateway forwards the request to the public API service, which then processes the request and accesses the database as needed.
In essence, API Keys are for identifying the application making the request.
🛡️ The Token Flow: Access for Logged-In Users
A Token, such as a JSON Web Token (JWT), is like a temporary, sealed passport issued directly to an end-user after they successfully log in. It proves the user’s identity and permissions for a limited time.
Simplified Token Flow (e.g., JWT):
* Login: An end user logs into the frontend web application (e.g., on AnalystGuru.in).
* Authentication: Login credentials are sent to the Identity Service.
* Token Issuance: On successful authentication, a JWT token is issued and returned to the frontend.
* API Call: The frontend makes subsequent API calls, placing the JWT in the Authorization header.
* Validation: The API Gateway intercepts the request and validates the JWT (checking the signature to ensure it hasn’t been tampered with, verifying its expiry time, and checking the claims/permissions inside).
* Forwarding: If valid, the gateway sends a validation response and forwards the request to the user-authenticated service.
* Processing: The service processes the request, interacts with the database, and returns the results to the user.
In essence, Tokens are for identifying the logged-in user making the request.
Understanding these flows is crucial for securing your analytical tools and data services. Use tokens to manage user sessions and API keys to manage third-party integrations—and always remember to keep both of them secure!